Part 2 — Financial Fraud: What You Need to Know to Protect Your Business
Part 1 of this article series examined various types of business fraud and how they are contributing to the recent, rapid increase in instances of business fraud. Here, we will look at how companies can reinforce their defenses against fraud by implementing a multi-layer fraud risk assessment framework.
What is a fraud risk assessment framework? In a nutshell, it’s a process that helps pinpoint areas where an organization may be vulnerable to fraud so it can develop concrete fraud mitigation plans. Conducted correctly, a fraud risk assessment framework keeps the business a few steps ahead of fraud perpetrators by viewing the company holistically from a fraudster’s perspective. The framework guides the effort to answer questions such as: where do we have weaknesses in our controls that could be exploited? And in what ways could our organization inadvertently be helping fraudsters escape detection?
To be effective, a fraud risk assessment framework has to have several foundational, data-driven layers. The first layer comprises the effort to accurately identify potential customers or third parties — who they actually are, and whether they present possible risks or discrepancies based on company data. The second layer involves scrutiny of the digital identity markers associated with those entities — electronic credentials that will help establish a comprehensive business fraud risk profile during real-time transactional processes.
First layer: verifying identity — is this a legit business?
The point when a business or supplier initiates a new business relationship is the best time to conduct the necessary due diligence to verify a company’s legitimacy. This process relies on data — optimally, data that has been rigorously vetted using multiple sources to ensure the business genuinely and uniquely exists.
Fraudsters will fabricate, exaggerate, or even omit certain data elements to make their business look more established. For example, a business may claim it started operations in 2015. But reliable data sources show that this business was actually created in 2021. By claiming 2015 as the business incorporation year, the fraudster could then exaggerate the annual employee count, sales revenue, or operational volume so the overall business profile appears to be more credible — thus creating opportunities for the entity to conduct fraud.
Investigating an entity’s address is an important identity verification step. Typically, higher risk is associated with virtual office locations, P.O. boxes, residential addresses, and freight forwarding addresses for a business transaction.
Key questions to ask during this phase of fraud risk assessment include:
- What is the firmographic information for the business, and can it be verified?
- Businesses don’t commit fraud, individuals do — so can we identify the individuals behind the business?
- Is the business identity legitimate or synthetic?
- Were the principals involved in any previous, now-defunct businesses?
- What products are they purchasing, and does it make sense for this business to do so?
Second layer: uncovering risks behind a device, IP, or email address
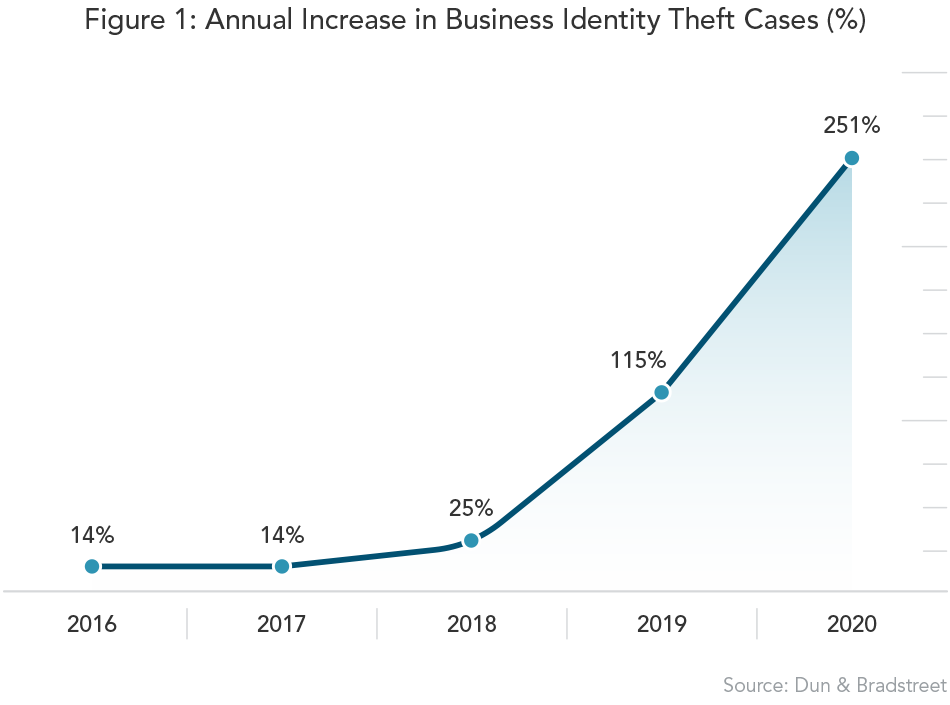
When the global pandemic brought the physical world to a grinding halt, fraudsters took advantage of the moment. Dun & Bradstreet data shows a 251% increase in business identity theft in 2020, compared with 2019 (Figure 1). This spike is strongly correlated with dramatic increases in digital transaction volumes and related cyberattacks. More consumer identity data getting into the hands of bad actors translates to more occurrences of business-to-business fraud.
Typically, fraud rings use a handful of IP addresses or hosts and cycle through a long list of stolen user credentials to breach a company’s security/fraud defenses. For this reason, assessing fraud risk based on the email, domain, phone number, or device and IP address being used for transactions is critical.
In particular, email age is a telling risk indicator. For example, an email address established two days before it was used in a commercial loan transaction would be highly irregular. Data analysis has shown a higher incidence of fraud activity connected to newer emails.
For instance, if a real business domain is abcpizza.com, a fraudster might create abcpizzainc@pizzaparlor.com, instead of first.last@abcpizza.com. In one real-world example, a fraudster placed a large order for restaurant equipment, and instead of using the real business domain abcpizza.net, the fraudster used the “look-alike” of abcpizza.us.
When researching a domain as part of a fraud risk assessment, a best practice is to look at the “whois” information. It will be important to understand when the domain was created and compare that date against the company start date.
The device profile will need to be captured real time to evaluate device risk. Key considerations include device age, velocity, reputation, and device IP.
- Device age will detect a device new to the network.
- Device reputation is highly effective in identifying devices previously used for fraud.
- Velocity will gauge If the same device is being used to create multiple accounts within a short period of time.
- Device IP can detect geolocation mismatches between the business’s operating location and the device location.
One benefit of using device risk data is that the device ID provides anonymous computer characteristics, rather than personal information, to help create a digital profile for fraud detection. If a business account has already been rejected due to suspicious behavior, and the fraudster uses the same device to apply for another account under a different name, the organization will know right away because the returning device can be verified.
A comprehensive fraud risk assessment framework is much broader than what has been described here; organizations also need to examine their existing fraud control processes, map them to different fraud schemes, and implement appropriate activities to remediate fraud control gaps. But having quality data that can authenticate an entity’s physical and digital identities, and thus prevents fraudsters from gaining access to the business, saves valuable time and intercepts many major fraud schemes before they can cause real financial and reputational damage.
In our next and last article in Dun & Bradstreet’s Business Fraud series, we’ll discuss the importance of leveraging industry negative lists and evaluating business entities’ operating and financial status as a critical part of your comprehensive fraud risk assessment.
The information provided in articles and blog posts are suggestions only, based on best practices, and provided as-is. Dun & Bradstreet is not liable for the outcome or results of specific programs or tactics. Please contact an attorney or tax professional if you are in need of legal or financial advice.
